While working on a client’s Azure subscription(s) I found that my CSP privs weren’t giving me owner permissions through Partner Center. This was due to the fact that the client had multiple subscriptions and only one of them was created by my firm through Partner Centers. The other was a retail, Azure Plan sub. I wanted to have the engineers in my firm admin the subscription with their partner tenant account rather than an in-tenant GA. This promotes better audit logs and supports RBAC permissions.
DAP permissions (and GDAP if you configure them as such) give AAD Global Admin permissions to members of a group within the partner tenant. Being an AAD Global Admin (outside of certain configurations does not inherently grant you access to an Azure subscription in that tenant. When a subscription is created through Partner Center, the Owner role is granted to a “Foreign Principal” object in the customer tenant that represents the AdminAgents AAD group in the partner tenant. You cannot see this “Foreign Principal” in the standard group selection tools but it does display on the Role Assignments list
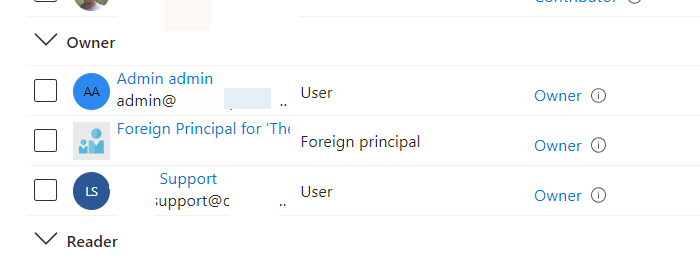
I found this Microsoft Learn article about re-adding those permissions if someone with the ability were to remove them. AdminAgents permissions have always been very broad. A member of that group instantly has god rights over large swaths of customer environments. Armed with the syntax in the article I thought I would be able to create a new group, grab its GUID and run the command in the customer tenant to grant privs to whatever group I wanted. Not so much. I recieved this error when trying to use new-azroleassignment to a group other than AdminAgents

Not very descriptive – “BadRequest.” If we add -debug we get much better information

The error notes that the object “does not exist in the directory” (the target directory). No kidding! That’s the point! Given that the command even has the flag -ObjectType "ForeignGroup" this seemed an odd error to me.
There is not a ton of information out there on the AdminAgents group under the hood. Best I could find was this Partner Community article with an answer by the very knowledgeable Janosch Ulmer from Microsoft. I reached out to Mr. Ulmer on LInkedIn asking what was unique about the AdminAgents group. He was kind enough to confirm that “It is indeed hardcoded that only those two groups work for the foreign principal” (AdminAgends and HelpDesk Agents). His suggestion for “the way” to achieve my goal is to move to Azure Lighthouse. Surely the right answer, but a larger lift for another day.
You can use this method, however, for accessing subscriptions in client tenants that were not originally created in CSP. So, if you inherit a client that already has a subscription and for $reasons you can’t move things to a new, fresh CSP subscription but want to use Partner Center for RBAC, you can use the syntax from the Learn article. You must have a reseller relationship with the client for this to work.
From the partner tenant
get-azadgroup -DisplayName "AdminAgents"From the client tenant
#Enter primary client domain (might not be onmicrosoft.com)
$clientDomain = "domain.com"
#Enter subscription ID to be granted privs
$clientSub = "87a636ee-XXX-YYYY-8ac3-700394a2f6bf"
Connect-AzAccount -Subscription $clientSub -TenantID $clientDomain
New-AzRoleAssignment -ObjectID "ID FROM PARTNER TENANT" -RoleDefinitionName "Owner" -Scope "/subscriptions/$clientSub" -ObjectType "ForeignGroup"TL;DR
AdminAgents is a special group name that can do Foreign Principal magic. Other groups are domestic only.
Isn’t it required to be an Owner on the subscription to run this script to enable Owner on the CSP’s foreign principal?
Thats a good call out, if you’re locked out with no in-tenant access at all, you would not be able to do this.